Elastio’s Model Context Protocol (MCP) Server embeds agentless ransomware detection and backup validation directly into AWS workflows, developer tooling, and AI assistants, with claimed zero-day detection capability.

The company was founded in 2020 by CEO Najaf Husain and CRO Todd Frederick to combat zero-day ransomware threats that evade traditional defenses by cloud-native SW running agentless detection, malware scanning of backups, automated recovery testing, and immutable storage to enable rapid, clean restores after malware detection. Husain previously founded data center composability business Cloudistics whose assets were bought by Fungible in 2020. Husain started up AppAssure before that and it was acquired by Dell in 2012. Elastio started out with a seed round in 2020 and then raised $18 million in a mid-2023 A-round.
Greg Aligiannis, CISO at Elastio, stated: “With the MCP Server, we bring detection, validation, and compliance-ready reporting straight into the environments teams already use.”

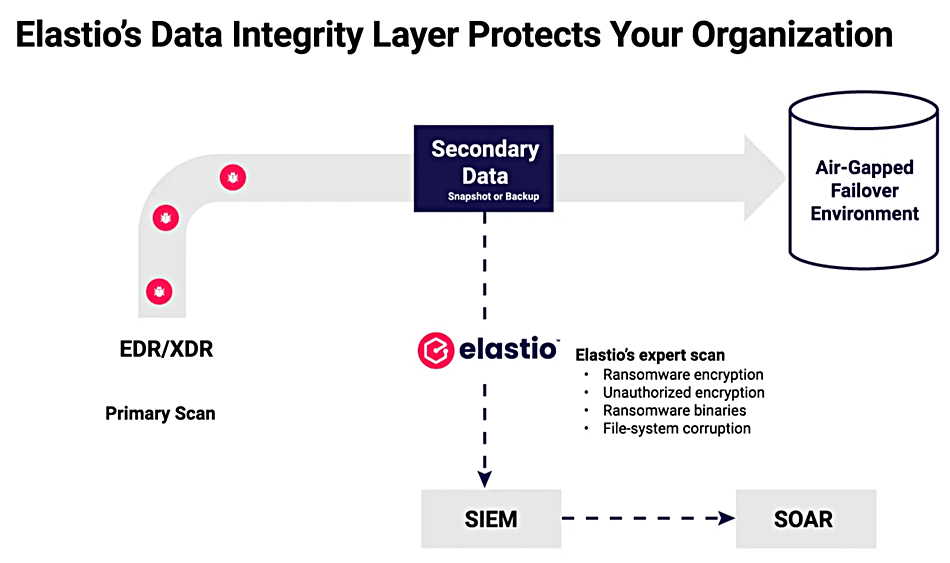
The MCP Server has been developed with the idea that modern enterprise operations will increasingly depend on agentic AI workflows, autonomous systems where AI agents reason, act, and adapt with minimal human oversight. These dynamic workflows orchestrate, correct, and recover in real time but need real-time cyber-resilience. Elastio claims its MCP Server makes incident response, resilience, and recovery an integrated part of agentic workflows and enables self-healing.
It provides:
- Managed cyber resilience: Continuously monitor backups, restores, deployments, and files, directly within IDEs, AWS workflows, and chat-based AI assistants,.
- Agentic and extensible: Integrates across ecosystems as MCP delivers resilience data into agentic tools and platforms, exposing compromised data caused by ransomware, misconfigurations, and optimization opportunities in real time.
- Incident response with real-time detection and live context: Gain continuous visibility at the asset, volume, and file level, identifying threats as they emerge and delivering live context through AI assistants to accelerate response and “guarantee uncompromised recovery.”
Which backups does it constantly monitor and how does it identify them? The two main targets are AWS and Azure. On AWS, it says it monitors recovery points for EC2 instances, EBS volumes, EFS file systems, S3 object storage, and VMware workloads created via AWS Backup. It also inspects snapshots and data in logically air-gapped vaults. There are integrations with Cohesity, Commvault, NetBackup, Rubrik, and Veeam backup, allowing validation of their backup data for ransomware and malware presence.
Elastio scans AWS accounts and integrated environments to detect new workloads, resources, and backup instances dynamically via IAM roles, SQS messages, and Lambda invocations, with no direct VPC connectivity. This triggers inspection of eligible backups without agent installation. Backups are identified through API integrations with AWS Backup and third-party tools, correlating them to specific assets (e.g., EC2/EBS recovery points). It uses metadata like resource IDs, timestamps, and storage locations to catalog and track backups.
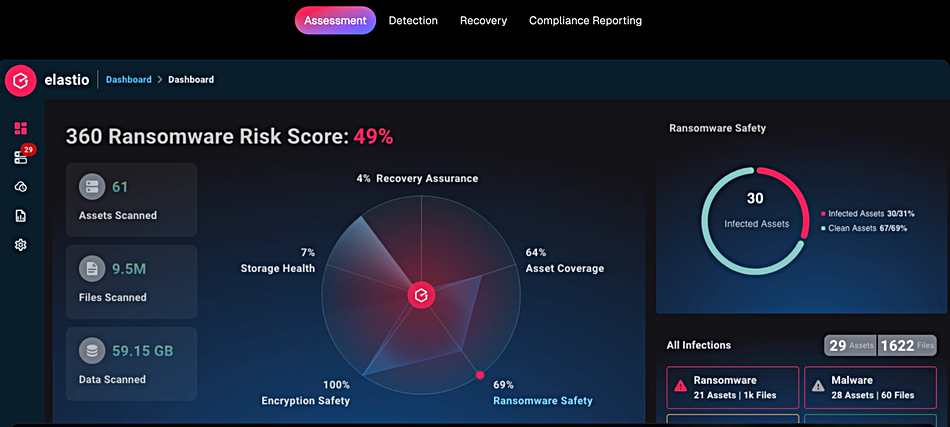
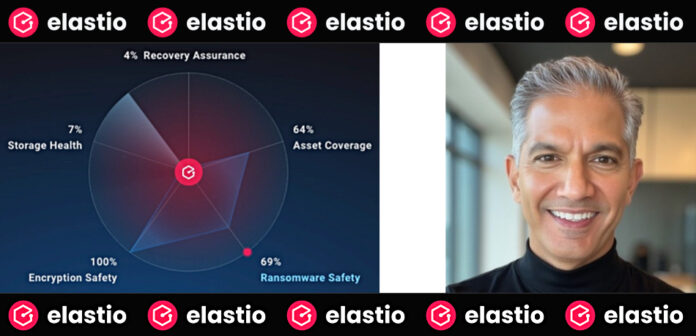
We understand that backups are scanned using RansomwareIQ, Elastio’s data integrity engine, which employs machine learning for behavior-based detection (beyond signatures or anomalies). This includes heuristics, detonation in isolated environments, and forensic mounting (read-only) to verify integrity, quarantine infected points, and pinpoint the last clean recovery state. RansomwareIQ mounts backups in a secure, read-only environment and uses ML-driven analysis to detect ransomware signatures, encryption anomalies, and behavioral red flags. Infected recovery points are flagged and isolated, preventing restoration of compromised data. Then it provides detailed reports on threat exposure, clean recovery points, and compliance status, accessible through Elastio’s unified dashboard.
The MCP Server will also soon integrate with Azure Backup, Azure Site Recovery (ASR), Azure Blob Storage, Azure VMs, and Azure Block Storage, and has full support for Veeam backups stored in Azure. It says it will inspect Veeam backups stored in Azure Blob Storage, “detecting encryption patterns and insider threats that often slip past antivirus or EDR tools.” Request an preview of Elastio on Azure here.

The MCP Server can provide monitoring and clean recovery from third-party on-premises backups, where integrated. We understand that these include Cohesity DataProtect and (Veritas) NetBackup, Commvault Complete Data Protection, Rubrik CDM, and Veeam Backup & Replication.
Existing Elastio customers include the Boston Celtics, healthcare IT provider Cloudwave, legal tech SaaS company CARET, and a global payment business handling >40 billion transactions annually.
The Elastio MCP Server for AWS is available today, with installation guides and documentation. Continuous feature updates and integrations will be released via AI-assisted channels. Read more about Elastio’s software in its blog and solution brief docs.