HyperBUNKER provides a backup of backups, and air-gapped, offline, multiple immutable data copies as a last resort for solidly dependable critical data recovery.
Data is written using data diode technology to a target device operated by PLCs (programmable logic controllers). It has its own backup software for file storage and is thus an addition to existing backup software. The data diode technology enforces a one-way, data-in communications path to the HyperBUNKER vault device. This technology is commonly found in highly-secure power grids, water utilities, nuclear facilities, and military installations, but has not been seen in traditional enterprise data protection and cyber-resilience products. The company was founded as an offshoot of data recovery business InfoLAB in Zagreb, Croatia, by CEO Bostjan Kirm and CTO Imran Nino Eškić. Nino Eškić is InfoLAB CEO.
Investor and advisor Matt Peterman told us why he became appreciative of the HyperBUNKER concept: ”You see servers and drives shipped in [to InfoLAB] from all over Europe – companies locked out of their own data. And why does this happen if they have perfect cyber protection tools? Sometimes, it is due to hardware failure, and often due to ransomware. And in those ransomware cases, Nino could do very little except suggest negotiating through brokers. That frustration is what pushed him to design an offline protection that actually preserves the most critical data.”

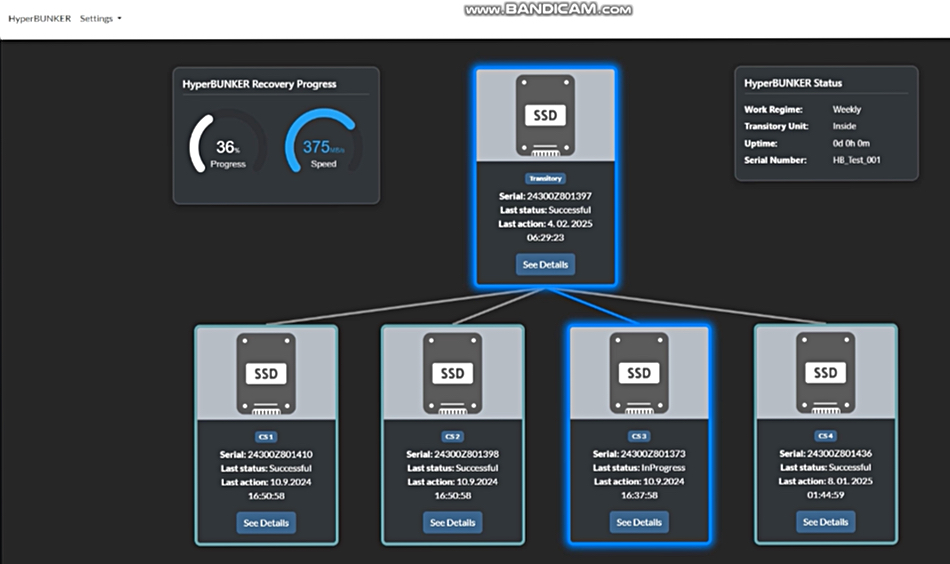
The key tech is the data diode idea, applied while a backup is being written to the HyperBUNKER rack-shelf chassis’ SSDs or disk drives. The company says this is disconnected from the external networks, such as the internet. Its software performs a comprehensive backup of entire hierarchical folder structures, such as a NAS system, preserving all subfolders and their contents. During recovery, which uses a separate access path, the original structure is fully restored.
The device uses optocoupler-isolated monitoring, whose signals prevent unauthorized access. It says its tech remains invisible within network infrastructures, making it undetectable and unreachable to online hackers.

Peterman tells us: “This is not a new technology. But in practice, traditional diodes are one-way network devices. They still rely on protocols, handshakes, and ultimately leave the protected side online. One bad update or exploited protocol – and the vault is exposed. Three years ago, Nino tested diode systems extensively, then developed a different approach: optical isolation and butlering logic. That’s what HyperBUNKER patented in October 2024. It means data is kept physically offline at all times, no dependency on network protocols, no exposure to handshake exploits.
He says there are public examples of existing cyber-protection failing: “Public cases back this up. Capital Health (Rubrik, LockBit 3.0), Community Health Systems (Rubrik, CL0p), Veeam client breaches, even NHS repeat failures. Tools passed ‘compliance,’ but when tested by real incidents, backups collapsed or were bypassed. See also recent M&S and Jaguar case.”
Peterman said HyperBUNKER tracks “65-plus ‘cyber protection’ tools in the market, but ransomware is still growing.”
“From my background in insurance fraud detection (my previous investment), the contrast is striking. In fraud, we always knew why a case failed, whose fault it was. In a cyber attack, postmortems are often not revealed or shared. The more complex the stack, the more likely a human or config error opens the door. HyperBUNKER is built for simplicity: if my most critical data is in my desk drawer, there’s very little chance a North Korean actor can lock it.”
HyperBUNKER admits “the only vulnerability is the physical theft of the device. However, by distributing HyperBUNKER units across multiple locations and encrypting all stored data, the risk of data compromise is minimized.” We asked HyperBUNKER some questions.
B&F: What is the data diode technology about?
HyperBUNKER: Inbound writes traverse optocouplers that physically enforce one-way flow. Data can enter the vault but nothing electronic can come back out. There is no logical bypass.
B&F:What are the dedicated PLC electronics used for storage management?
HyperBUNKER: Independent micro-PLC controllers govern drive power states, media rotation, and write windows. They are air-gapped and cannot be reached or reprogrammed over a network, so ransomware cannot flip modes or trigger erasures.
B&F: When existing backup software can write to tape libraries, with offline tape cartridges, why do I need HyperBUNKER?
HyperBUNKER: Tapes are only “offline” once ejected. During write or restore the library and control plane are online with credentials exposed. HyperBUNKER’s vault media are never network-addressable. Inbound is one-way optical so there is no session to hijack and no remote delete. And restoring data from tapes can last for a while.
B&F: If I use HPE Zerto why do I need Hyperbunker?
HyperBUNKER: Zerto is strong software but it lives on the network and depends on credentials, updates, and policy. HyperBUNKER sits outside that plane as a last-resort, physically isolated vault when software defenses are breached.
B&F: What prevents the HyperBUNKER backup software backing up already corrupted data? How do you know the backup is clean?
HyperBUNKER: HyperBUNKER does not try to detect malware or decide what is clean. It is content-agnostic by design. Protection comes from physically enforced immutability and spaced generations. New writes cannot alter or delete earlier sets. If a poisoned write reaches the vault, it lands as a new generation, and recovery means selecting a pre-event generation upstream. But you can do numerous “restores” of data in a virtual environment and remove malware. That’s what Nino is quite often doing in his data recovery labs in Verona and Zagreb.
B&F: How is HyperBUNKER priced? By capacity? What is its capacity?
HyperBUNKER: Appliances are priced by usable capacity, not per-seat or license. Current ranges are 1 TB and 4 TB configurations. Typical entry deployments start around €50,000.
Bootnote
HyperBUNKER incorporates encryption, access controls, and regular audits to meet GDPR and other privacy standards. It employs a proprietary version of File Security Encryption (FSE), meets HIPAA standards for protecting electronic protected health information (ePHI) and complies with PCI DSS requirements, ensuring secure storage for payment card information with encryption and restricted access. HyperBUNKER aligns with the NIS2 Directive. A rugged, military-grade version with EMP/EMI protection is planned.








