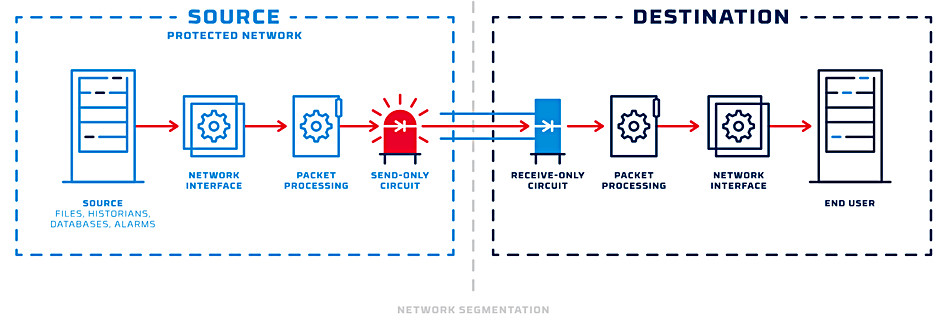
Data diode – a one-way data transmission technology. A diode is a one-way electrical valve device that passes current one way, having low resistance, but not the other way, having very high resistance in that direction. A data diode is a cybersecurity device or subsystem that enforces one-way data flow between two networks or a network and a device, ensuring data travels only in a single direction. It’s typically implemented as a hardware-based system with a physical or logical barrier, preventing any reverse communication. This creates an “air gap” effect, allowing data to move from a less secure network to a more secure one (or vice versa) without risking backflow or unauthorized access. The diode physically or logically blocks any data, signals, or packets from flowing back to the source.
It prevents data leakage, malware propagation, or external attacks by eliminating bi-directional communication. Many data diodes strip or transform data to ensure compatibility and security across different network protocols.
Data diodes protect systems like power grids, water utilities, or nuclear facilities by isolating sensitive control networks. They secure classified networks while allowing controlled data exportand enables organizations to share data with external partners without compromising internal security.
Ensuring correct data receipt
Ensuring correct data receipt with unidirectional communication, which prevents acknowledgment or feedback from the receiving side, has challenges. The lack of a return channel means the sender cannot receive immediate confirmation of successful delivery. Assurance relies on proactive measures at the sender and receiver. If data packets are lost, the receiving system may detect gaps via sequence numbers, but resolving this often requires manual intervention or retransmission policies. Validation and error-checking processes can introduce slight delays, which must be accounted for in time-sensitive applications.
In high-security environments (e.g., military or critical infrastructure), assurance is often achieved by combining multiple methods—checksums, redundant transmissions, and periodic out-of-band audits. For example, a nuclear facility might use a data diode to send sensor data to an external analytics system, with the receiving system checking data integrity via hashes and logging any anomalies for later review. If absolute assurance is critical, organizations may implement redundant diodes or manual verification processes.
Here are some mechanisms and practices used to provide assurance of correct data reception in data diode technology:
1. Error Detection and Correction at the Source
- Checksums and Hashing: Before transmission, data is often appended with checksums (e.g., CRC32) or cryptographic hashes (e.g., SHA-256) to verify integrity. The receiving system can compute the checksum or hash and compare it to ensure the data wasn’t corrupted during transfer.
- Forward Error Correction (FEC): Some data diodes implement FEC, embedding redundant data in the transmission to allow the receiving side to detect and correct errors without needing a return channel.
2. Protocol Conversion and Validation
- Data Validation: Data diodes often include protocol break mechanisms that parse and validate data at the diode’s input and output stages. For example, the diode may check that the data adheres to expected formats (e.g., XML, JSON) before forwarding it.
- Reformatting: The diode may reformat or sanitize data to ensure compatibility with the destination system, reducing the chance of errors due to protocol mismatches.
3. Redundant Transmission
- Multiple Sends: To increase reliability, the source system can send the same data multiple times. The receiving system may compare these copies to identify and correct discrepancies, assuming it has logic to handle duplicates.
- Time-Stamped Sequencing: Data packets can include sequence numbers or timestamps, allowing the receiving system to detect missing or out-of-order packets.
4. Monitoring and Logging
- Sender-Side Logging: The sending system logs all transmitted data, including timestamps, sizes, and checksums. If a separate monitoring channel exists (e.g., a physically isolated logging system), it can be used to verify what was sent.
- Receiver-Side Verification: The receiving system logs incoming data and checks for completeness and integrity using embedded error-detection codes. Discrepancies can be flagged for manual review, though not communicated back due to the diode’s one-way nature.
5. Out-of-Band Verification
- Separate Channel for Assurance: In some setups, a completely separate, secure, and often manual process (e.g., physical media transfer or a dedicated monitoring system) is used to confirm receipt. For example, an administrator might check logs on both sides to ensure data consistency.
- Audit Trails: Both sender and receiver maintain detailed audit logs, which can be compared periodically through an out-of-band process to confirm successful transfers.
6. Reliable Transport Protocols
- UDP-Based with Enhancements: Many data diodes use UDP for one-way communication due to its simplicity and lack of return traffic. To compensate for UDP’s lack of reliability, custom protocols or applications (e.g., Data Distribution Service) add sequence numbers or retransmission logic at the application layer on the sending side.
- File-Based Transfers: Instead of streaming data, some systems transfer complete files with built-in integrity checks (e.g., file hashes). The receiving system verifies the file’s integrity upon receipt.
7. System Design and Testing
- High-Reliability Hardware: Data diodes are often built with robust hardware (e.g., optical fiber for physical separation) to minimize transmission errors. Optical diodes, for instance, have very low bit-error rates.
- Pre-Deployment Testing: Systems are rigorously tested to ensure the diode and associated software handle data correctly under various conditions, including high loads or corrupted inputs.
- Redundancy: Some setups use multiple data diodes in parallel, sending the same data through each. The receiving system compares outputs to ensure consistency.







